Introduction
If you are shipping AI features inside a SaaS product, you are almost guaranteed to touch PII. Sometimes directly, like user profiles. Sometimes indirectly, like chat logs, support tickets, call transcripts, screenshots, or “harmless” analytics events.
Now add a boilerplate. You move fast, which is the point. But you also inherit defaults you did not choose: verbose logging, generous retention, third party SDKs, and “we will clean it up later” data flows.
This article is a field guide for consulting engineering leaders building enterprise grade AI SaaS in regulated industries. It focuses on PII handling, retention, and compliance workflows that still let you ship.
You will see tradeoffs. Some patterns work. Some fail quietly until procurement, security, or legal asks one question you cannot answer.
- We will talk about GDPR, HIPAA, and PCI DSS.
- We will cover what to bake into a boilerplate on day one.
- We will outline workflows that keep stakeholders aligned without slowing delivery to a crawl.
Insight: If you cannot explain where PII enters, where it is stored, and when it is deleted, you do not have privacy by design. You have hope.
What “privacy by design” means in AI SaaS (in practice)
For AI SaaS, privacy by design is not a policy document. It is a set of engineering defaults:
- Data minimization: collect less, not “collect and redact later.”
- Purpose limitation: every field has a reason to exist.
- Controlled retention: time boxed storage, enforced automatically.
- Auditable access: you can prove who accessed what, and why.
- Safe AI integration: prompts, tool calls, embeddings, and model logs are treated as production data flows.
A good test: could a new engineer join the team and answer these questions in 30 minutes?
- What PII do we process?
- Where does it travel?
- What is the legal basis and purpose?
- How do we delete it end to end?
- What happens when an LLM provider changes a default?
Boilerplate privacy hardening checklist
Quick wins before the first enterprise demo
- Disable verbose request logging in all environments
- Add structured logging with a redaction allowlist or denylist
- Turn off session replay and aggressive analytics by default
- Add a vendor inventory file and dependency review step
- Separate PII storage from general app data (even if it is one database schema)
- Define retention classes and implement a daily purge job
- Add deletion request flow and event based propagation
- Document model provider data handling defaults and verify configuration
Where privacy breaks when you ship from a boilerplate
Boilerplates save weeks. They also ship opinions you did not review. In regulated environments, the failure mode is rarely “we got hacked.” It is usually “we cannot pass security review” or “we cannot answer the auditor.”
Common breakpoints we see when teams move fast:
- Logs become a shadow database (request bodies, headers, prompt text, error traces).
- Analytics SDKs collect identifiers by default (device IDs, IP, user agent, session replay).
- Background jobs keep data forever because nobody owns retention.
- Vector databases and embeddings store sensitive text that was never classified.
- Customer support tooling becomes a data exfil path (tickets with PHI, exported CSVs).
Key Stat (hypothesis): In early stage AI SaaS builds, 30 to 50 percent of “stored PII” ends up outside the primary database (logs, analytics, support exports). Measure it by sampling and classifying 1,000 recent events across systems.
Regulated industry constraints that change the game
Finance, healthcare, and defense have different acronyms, but the engineering constraints rhyme:
- You need provable controls, not “we intend to.”
- You need bounded blast radius when something goes wrong.
- You need repeatable workflows for access, deletion, and incident response.
Here is the practical implication: privacy decisions cannot live in a single document. They must live in code, CI, and daily ops.
A quick comparison: what each framework tends to force
| Framework | What it cares about most | Engineering implication | Common AI SaaS pitfall |
|---|---|---|---|
| GDPR | lawful basis, minimization, rights, cross border transfers | data inventory, deletion workflows, DPA and SCC readiness | prompts and model logs treated as “not personal data” |
| HIPAA | PHI safeguards, access controls, auditability, BAAs | strict access, audit logs, vendor contracts | using an LLM vendor without a BAA for PHI |
| PCI DSS | cardholder data security, segmentation, logging, testing | isolate payment flows, reduce scope, prove controls | storing PAN in logs or support tickets |
featuresGrid: Failure modes we flag in boilerplates
- Verbose request logging on by default
- Single shared database for auth, app data, and AI artifacts
- No data classification tags in schemas
- No retention jobs or deletion hooks
- Third party SDK sprawl without a vendor inventory
- One size fits all environments (dev equals prod, just smaller)
A concrete example: permissions and platform constraints are privacy constraints
When we worked on Mersive, a big part of delivery was navigating strict OS permissions for screen recording on Android and iOS. That is not “privacy work” in the legal sense, but it is privacy by design in practice.
- The platform forces explicit consent.
- The app must handle sensitive content on screen.
- The failure mode is not just a crash. It is capturing more than the user expects.
The lesson carries to AI SaaS: consent, scope, and user expectation are product constraints that need engineering enforcement, not just UI copy.
PII handling patterns that survive enterprise review
This is the part teams usually underestimate. It is not enough to “encrypt the database.” You need a map of data flows and a set of safe defaults across ingestion, processing, storage, and export.
Start with a data inventory that engineers will actually keep updated
If the inventory is a spreadsheet nobody opens, it will drift. Make it part of the codebase.
Minimum viable inventory:
- Data category (PII, PHI, payment, operational)
- Fields and examples
- Source (UI, API, import, integration)
- Storage locations (DB, object store, logs, analytics, vector DB)
- Processors (internal services, vendors)
- Retention and deletion mechanism
Insight: The fastest way to lose stakeholder trust is to say “we do not store that” and then find it in logs.
Use a “PII boundary” service, even in a small system
In a microservices world, teams often overdo decomposition. But a PII boundary is one split that pays off early.
- Keep identity and sensitive attributes in a dedicated store.
- Use surrogate IDs everywhere else.
- Gate access through a single service with strict auth and audit.
This reduces scope for PCI DSS and makes GDPR deletion easier. It also simplifies vendor reviews because fewer systems touch sensitive data.
Redaction is not a strategy, but it is a useful tool
Redaction helps, but it fails in predictable ways:
- It misses edge cases (names, addresses, free text).
- It breaks product features (search relevance, debugging).
- It creates false confidence.
Use it where it fits:
- Before sending text to LLMs when you do not need identifiers
- In logs and error traces
- In support exports
Code example: structured logging with PII safe defaults
// Example: Node.js structured logging wrapper
// Goal: never log raw request bodies, tokens, or prompts by default.
type LogContext = {
requestId ? : string;
userId ? : string;
orgId ? : string;
route ? : string;
pii ? : "none" | "possible" | "confirmed";
};
const SENSITIVE_KEYS = new Set([
"authorization",
"cookie",
"password",
"ssn",
"pan",
"cvv",
"prompt",
"input",
"message",
]);
export function safeLog(event: string, data: Record, ctx: LogContext = {}) {
const sanitized: Record = {};
for (const [k, v] of Object.entries(data)) {
sanitized[k] = SENSITIVE_KEYS.has(k.toLowerCase()) ? "[REDACTED]" : v;
}
console.log(JSON.stringify({
event,
...ctx,
data: sanitized
}));
}What to measure (so this is not theater):
- Percentage of log lines containing emails, phone numbers, tokens
- Number of incidents where logs were used as a data source
- Time to fulfill a deletion request end to end
benefits: What good PII handling buys you
- Fewer systems in compliance scope
- Faster vendor and security review cycles
- Lower breach impact radius
- Less time spent on “data archaeology” during audits
LLM specific PII risks you need to name explicitly
AI adds new storage and transit paths that do not show up in classic SaaS diagrams:
- Prompt text and chat history
- Tool call arguments (often include identifiers)
- Model provider logs and debug traces
- Embeddings stored in a vector database
- Fine tuning datasets and evaluation sets
If you are in healthcare or finance, assume any free text can contain PHI or account data. Design accordingly.
Practical mitigations:
- Prompt templates that do not ask for identifiers
- Client side warnings and input constraints for sensitive fields
- Server side classifiers that tag content as possible PII
- Vendor configuration to disable data retention where available
- Separate indexes for sensitive and non sensitive embeddings
What usually goes wrong with LLM data handling
Failure modes we see during security review
- Prompts contain identifiers because templates were never constrained
- Tool calls leak customer data into third party logs
- Embeddings are treated as “not sensitive” and kept forever
- Debug traces and agent logs become a second system of record
- Evaluation datasets are built from production data without consent
Mitigation: treat prompts, traces, embeddings, and eval sets as first class data stores with retention, access control, and deletion.
Retention and deletion: make it boring and automatic
Retention is where good intentions go to die. The product ships. The database grows. Nobody wants to delete anything because “we might need it.”
PII boundary plus safe logs
Reduce scope, prove controls
Pattern that survives enterprise review: isolate sensitive data behind a small surface area. PII boundary service:
- Store identity and sensitive attributes in a dedicated store.
- Use surrogate IDs everywhere else.
- Route access through one service with strict auth + audit.
Logging defaults: never log raw request bodies, tokens, or prompts. Log only requestId, userId, orgId, route, and a pii risk flag (none, possible, confirmed). If you need debugging detail, add an explicit allowlist and time bound debug mode. Tradeoff: this adds one more service and a few more calls. Mitigation: keep the boundary thin (read, write, delete, export), and make deletion and access logs first class from day one.
In regulated industries, retention is not a preference. It is a control.
The retention model that works: default short, extend by exception
Set a baseline retention policy per data class:
- Authentication and billing records: longer (legal and accounting)
- Product telemetry: short (days to weeks)
- AI prompts and chat logs: short by default
- Support artifacts: time boxed and reviewed
Then allow exceptions with explicit ownership:
- Who approved it?
- Why is it needed?
- When does it expire?
Key Stat (hypothesis): Shortening default retention from 365 days to 30 days cuts the volume of sensitive data at rest by roughly 80 to 95 percent for most SaaS products. Validate by comparing monthly active users to stored event volume per retention bucket.
processSteps: A retention workflow you can ship from a boilerplate
- Classify data at creation (tag rows, objects, and events with a retention class)
- Set retention TTLs in storage systems that support it (object stores, some databases)
- Run a daily purge job for everything else
- Log deletions as events (what was deleted, when, and by which policy)
- Test deletion in CI (seed data, run purge, assert it is gone)
- Expose retention config to admins with audit trails
Deletion is not one button. It is a graph.
GDPR “right to erasure” and internal security requirements both force the same engineering reality: deletion must propagate.
Deletion targets usually include:
- Primary database rows
- Attachments in object storage
- Search indexes
- Vector database entries
- Analytics events (or at least user level deletion)
- Logs (often tricky, so you need a policy and a story)
A simple approach that works well:
- Use a deletion request table as the source of truth
- Publish an event like
user.deletion_requested - Each system subscribes and deletes its own data
- Track completion per system
Table: retention options for AI artifacts (prompts, chats, embeddings)
| Artifact | Default retention | When to keep longer | Safer alternative |
|---|---|---|---|
| Prompt text | 7 to 30 days | debugging a specific incident | store hashed fingerprints and structured metadata |
| Chat history | user controlled | user explicitly wants history | store summaries without identifiers |
| Embeddings | tied to source doc TTL | long lived knowledge bases | per tenant indexes with purge by doc ID |
| Model outputs | short | regulated record keeping | store only final user facing output, not full trace |
Insight: If you keep prompts for “quality,” you will eventually use them for training. That is fine, but only if you designed consent, review, and retention for it from day one.
What fails in practice (and how to mitigate)
Common retention failures:
- “We will add TTL later” becomes “we cannot delete because dependencies.”
- Backups are ignored until an auditor asks about them.
- Vector DBs have no deletion discipline, so stale sensitive text lingers.
Mitigations that work:
- Treat retention as a feature with acceptance criteria.
- Add a dashboard: records by retention class, purge lag, deletion queue depth.
- Write a one page backup policy: retention period, encryption, restore access, deletion story.
If you cannot delete from backups, be honest and document it. Many teams do a time based backup expiry plus strict access controls. It is not perfect, but it is defensible if it is deliberate.
Security questionnaire prep pack
Artifacts that save weeks of back and forth
- Data flow diagram with PII entry points and processors
- Retention table per data class, including backups
- Deletion and export workflow description with evidence (tests, logs)
- Vendor list with contracts (DPA, SCC, BAA where needed)
- Access control model and audit logging coverage
- Incident response runbook and on call ownership
Compliance workflows you can run without slowing delivery
Compliance is usually framed as paperwork. For engineering leaders, it is a workflow design problem.
Keep inventory in code
Make drift harder
A spreadsheet inventory dies fast. Put the data inventory next to the code that creates the data. Minimum viable inventory fields:
- Data category (PII, PHI, payment, operational)
- Field names + examples
- Source (UI, API, import, integration)
- Storage locations (DB, object store, logs, analytics, vector DB)
- Processors (internal services, vendors)
- Retention period + deletion mechanism
Failure to avoid: saying “we do not store that” and later finding it in logs. Add a PR checklist item: any schema change or new vendor must update the inventory file.
You need three things:
- A way to make decisions quickly
- A way to prove what you did later
- A way to keep it from regressing
A lightweight stakeholder cadence that works
In regulated enterprise work, alignment is not optional. But you can keep it tight.
Weekly 30 minute “privacy and security triage” with:
- Engineering lead
- Product lead
- Security or compliance owner
- Sometimes legal or procurement (as needed)
Agenda:
- New data flows introduced this week
- Vendor changes (new SDKs, new model providers)
- Open risks and mitigations
- Any upcoming customer security reviews
Insight: Stakeholders do not need more meetings. They need fewer surprises.
Turn compliance into pull requests, not slide decks
What we try to bake into delivery processes (especially when teams scale past MVP, as discussed in our work on post MVP operating models):
- A
data-flows.mdfile in the repo that changes with features - A vendor inventory file (name, purpose, data processed, contract status)
- A “PII checklist” in PR templates
- Automated checks in CI (lint for logging, secret scanning, dependency review)
faq: Questions enterprise reviewers will ask (and you should pre answer)
- What PII and PHI do you process, and for what purpose?
- Do you send any customer data to an LLM provider? Is it retained?
- Can you support data deletion and export per tenant?
- How do you restrict internal access to production data?
- What is your incident response timeline and logging coverage?
- Where is data stored geographically, and what transfer mechanisms do you use?
Mapping controls to delivery artifacts
You do not need to boil the ocean. You need a traceable chain:
- Requirement: “We must delete user data within 30 days”
- Design: deletion event and subscribers
- Implementation: purge jobs and handlers
- Evidence: tests, logs, dashboards, runbooks
If you can show that chain, audits become a review, not an excavation.
How enterprise architecture patterns help privacy (when used carefully)
Our enterprise architecture work often leans on microservices, event driven design, and zero trust. These patterns can help privacy, but only if you keep complexity under control.
What works:
- Microservices to isolate PII into one bounded context
- Event driven deletion to propagate erasure reliably
- Zero trust to reduce lateral movement and enforce per service auth
What fails:
- Too many services without consistent policy enforcement
- Observability systems that ingest everything, including sensitive payloads
Mitigation:
- Central policy libraries (auth, logging, redaction)
- Data contracts for events (no PII in event payloads unless required)
- Field level access rules enforced in one place
Examples from delivery: what we shipped, what we learned
Regulated AI SaaS work rarely allows public detail. But patterns show up across projects, even outside strict compliance domains.
Boilerplate privacy breakpoints
Where PII leaks first
Common failure mode: you cannot pass security review because you cannot answer “where does PII go and when is it deleted?” Breakpoints to audit in week one:
- Logs as a shadow database: request bodies, headers, prompt text, stack traces.
- Analytics SDK defaults: device IDs, IP, user agent, session replay.
- No retention owner: background jobs and exports keep data forever.
- Embeddings and vector DBs: sensitive free text stored without classification.
- Support tooling: tickets with PHI, CSV exports, shared inboxes.
Hypothesis worth measuring: 30–50% of stored PII lives outside the primary DB. Validate by sampling 1,000 recent events across logs, analytics, support, and object storage, then labeling them (PII, PHI, payment, none).
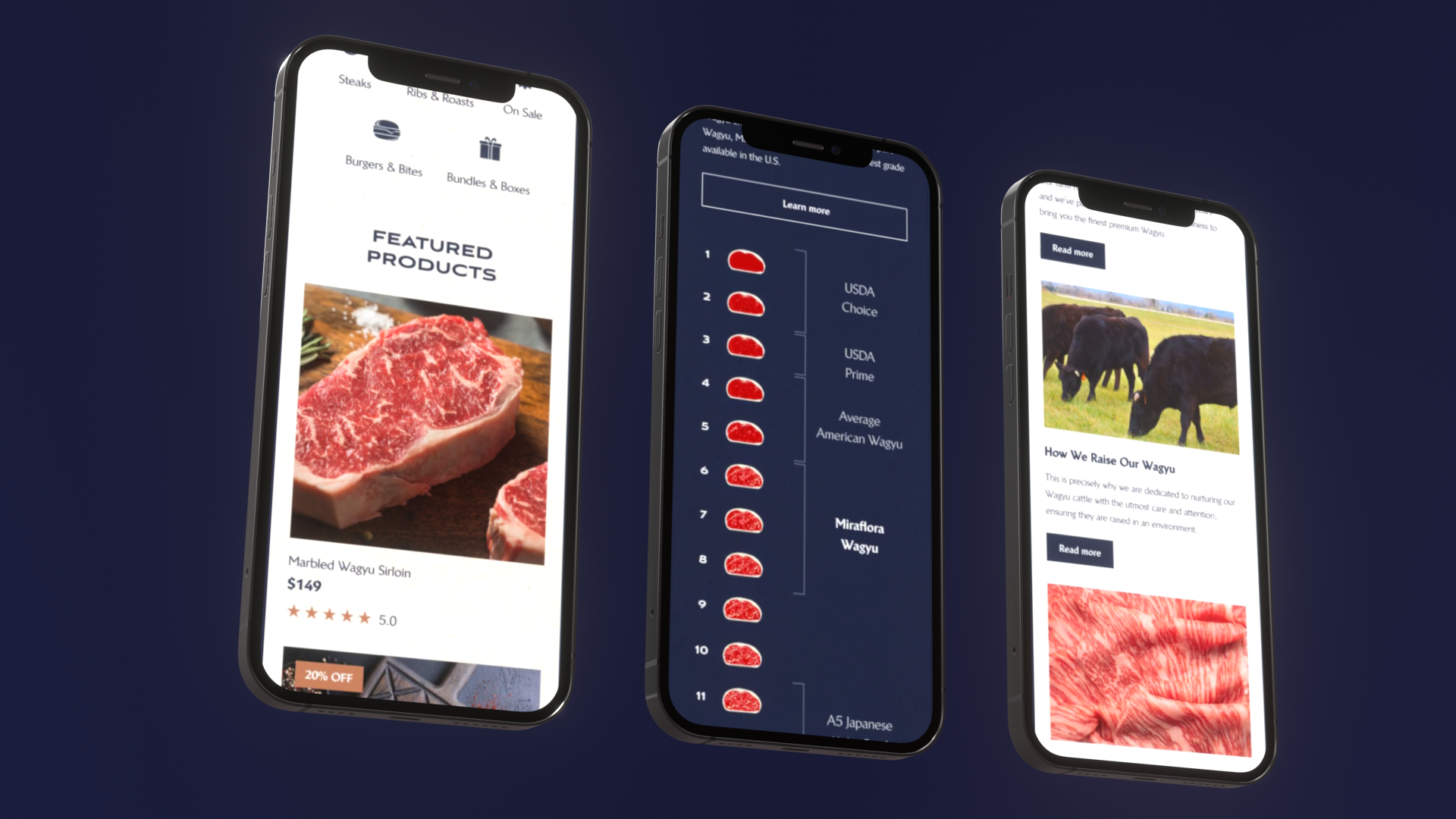
Shipping fast with guardrails: Miraflora Wagyu in four weeks
In our Miraflora Wagyu delivery, the constraint was time. The client team was distributed across time zones, and feedback was mostly async.
That kind of delivery pressure is exactly when privacy gets skipped. The mitigation is not “work slower.” It is make safe defaults the path of least resistance.
What this looks like in practice when using a boilerplate:
- Logging defaults that redact by design
- Minimal analytics until the data map is clear
- Explicit retention on uploads and customer exports
Example: When delivery is async and fast, you need fewer “please remember” rules and more “the code does it for you” defaults.
Permissions and user trust: lessons from Mersive
The Mersive mobile app work forced us to deal with strict OS permissions for screen recording and audio. It is an example of a broader point: privacy is an experience, not just storage.
For AI SaaS, the parallel is:
- Make it obvious when user content is sent to a model provider
- Make it clear what is stored and for how long
- Provide controls that work (download, delete, disable history)
AI prototyping vs enterprise readiness: Project LEDA as a cautionary tale
In our Project LEDA exploration, the goal was speed to prototype. That is the right move for learning.
The risk comes when prototypes quietly become production.
Typical transition gaps:
- Prototype prompts include raw customer data
- Evaluation datasets are copied into shared drives
- Agent traces are stored without retention
Mitigation:
- Add a “production gate” checklist: vendors, retention, audit, deletion, access controls
- Run a one day privacy review before the first enterprise pilot
Key Stat (hypothesis): The cost of retrofitting privacy controls after enterprise pilots start is 3 to 5 times higher than baking them into the boilerplate. Validate by tracking engineering hours spent on remediation across two comparable launches.
What to measure so you can prove outcomes
If you want measurable business outcomes, track the metrics that correlate with enterprise trust and delivery speed:
- Time to complete a customer security questionnaire
- Number of systems in scope for PII and PHI
- Mean time to fulfill deletion requests
- Percentage of logs and events flagged for PII leakage
- Vendor count with access to sensitive data
These metrics are not vanity. They predict whether you can close regulated customers without a six month detour.
Conclusion
Privacy by design for AI SaaS is not a document you add at the end. It is a set of defaults you ship from day one, especially when a boilerplate makes it easy to move fast in the wrong direction.
If you want a practical starting point, focus on three things:
- PII handling: know where data enters, keep it behind a boundary, and stop it from leaking into logs and vendors.
- Retention: default short, extend by exception, and automate purges.
- Compliance workflows: make decisions visible, tie controls to code, and keep evidence in the repo.
Next steps you can take this week:
- Inventory your data flows and vendors. Put it in the repo.
- Add redaction safe logging wrappers and CI checks.
- Implement deletion as an event, not a manual script.
- Set retention defaults for prompts, chats, and embeddings.
Insight: The goal is not perfect privacy. The goal is a system where privacy failures are hard to create, easy to detect, and fast to fix.
A simple readiness checklist for regulated pilots
- We can answer what PII and PHI we process per feature
- We can show retention per data class, enforced automatically
- We can delete a user or tenant end to end and prove it
- We have an audit trail for access to sensitive data
- We know which vendors touch data, under what contracts
- We have a runbook for incidents and customer questions